Say you have an API hosted on an EC2 instance & you want to make it publicly available. One obvious way to do this is to make the instance publicly accessible, but that’s not an ideal solution. Moreover, if we could put up API Gateway in front of this API, we could take advantage of its numerous features like authentication & throttling.
A VPC Link is the way to do this. Before VPC links came along, the only way to achieve this setup was to make the EC2 public & create an HTTP API integration to it in the API Gateway. VPC links let us keep our backend resources private inside the VPC & still route API requests to them. Thanks to VPC Links, the traffic between the gateway & the instance stays entirely inside the AWS network.
This article demonstrates how to implement the above setup in the simplest possible manner. Let’s start creating resources from the bottom-up. First, we have the instance hosting our API. Hit the API & you get back the ever so familiar, “Hello World!”:
Request: GET <EC2-IP>/hello Response: "Hello World!"
VPC links only support forwarding requests to resources behind an NLB, so create an internal NLB & register the instance as its target. Once this is done, you should be able to hit the API via the NLB:
Request: GET <NLB-DNS-Name>/hello Response: "Hello World!"
Now go to the VPC Links section of the API Gateway console & create a new VPC link:
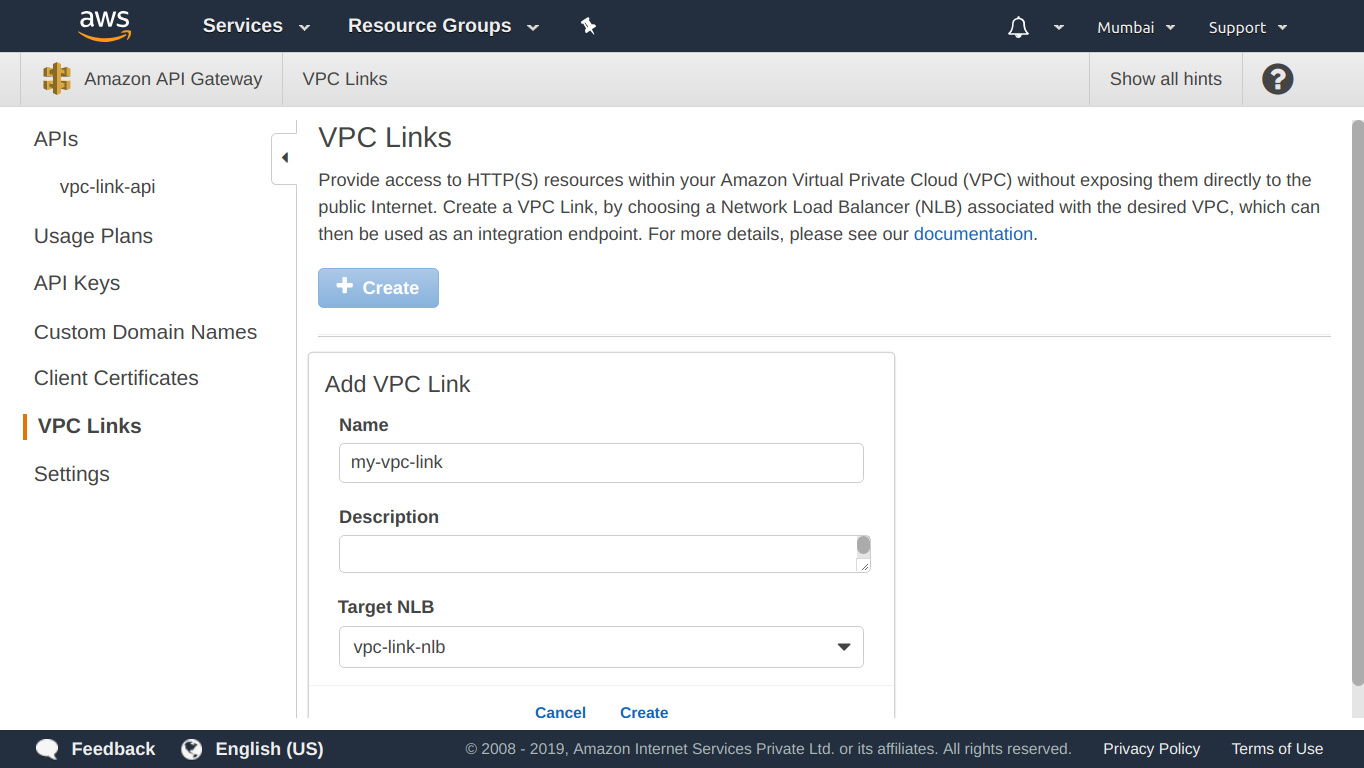
After the VPC link has finished creating, go to an API method & set its integration type as VPC link as shown below:
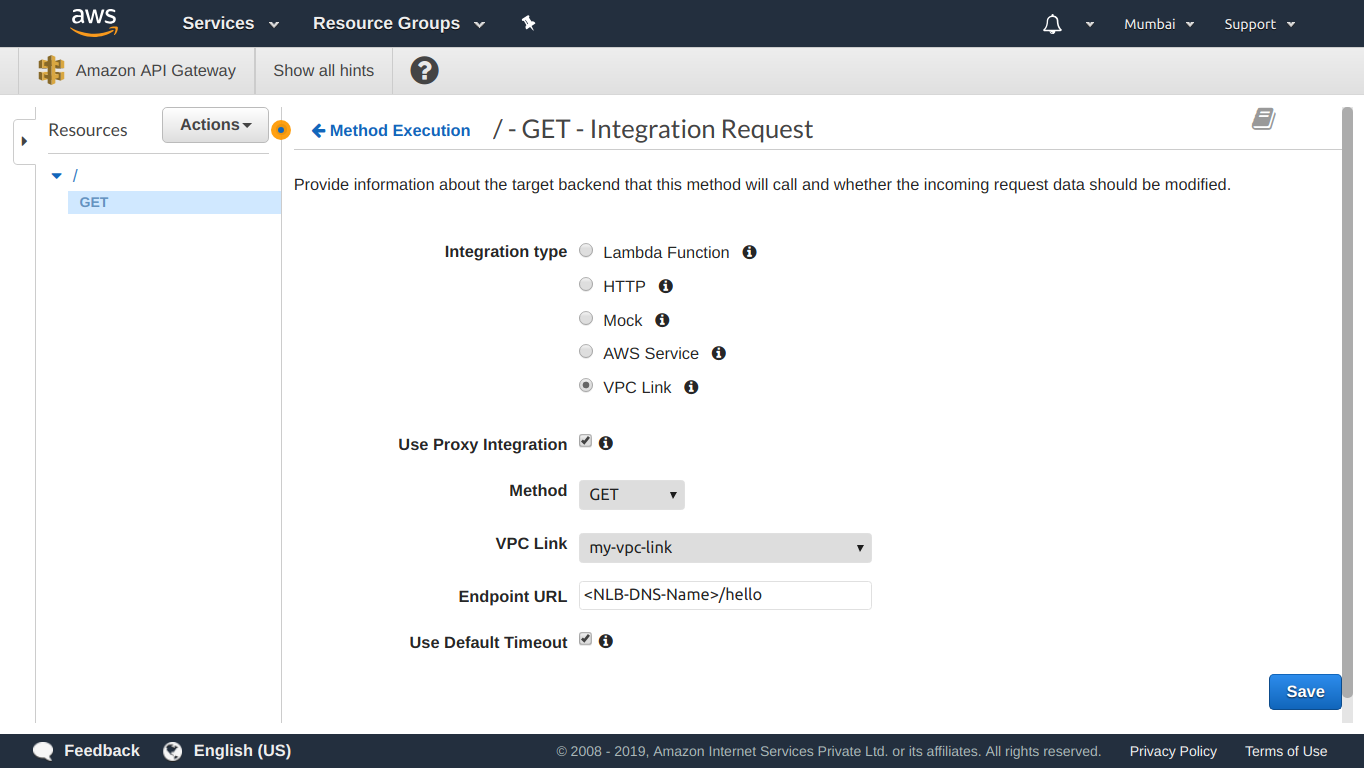
That’s it! Hitting this API endpoint now, should get us the response from the instance:
Request: GET <API-Endpoint> Response: "Hello World!"
(Part 4/6 in AWS series)






